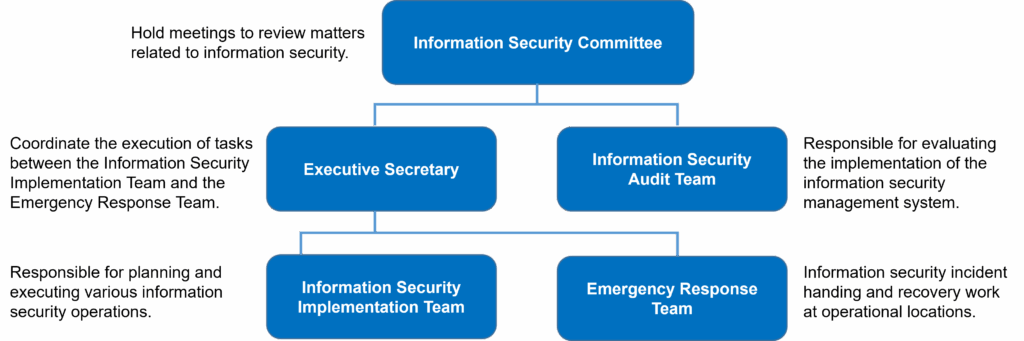
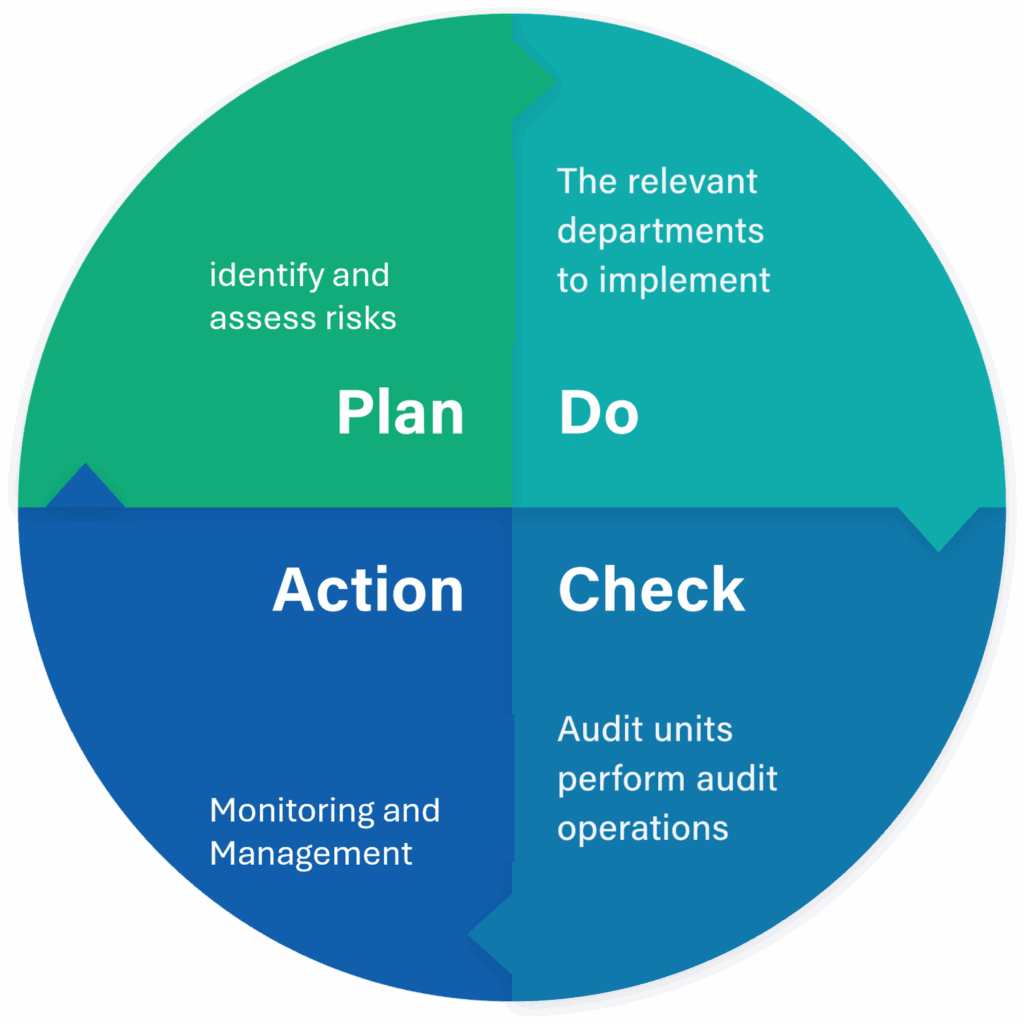
Specific management plans and resources devoted to cyber security management
The Company focuses on cyber security control, and the specific measures adopted are mainly based on five aspects of cyber security management:
01
Employee Management
At the time of employment, the Company signs a “contract of employment” with the employee, which stipulates that the intellectual property rights of all creations and inventions made by the employee during the employment period shall be vested in the Company. At the same time, the Company signs a detailed “confidentiality agreement” with the employee, which stipulates that the employee is responsible for maintaining the confidentiality of all business information, technology, processes, programs, procedures, designs or any other confidential information that the employee may use in the design, sale or operation of the Company, whether during or after the termination of the employment contract. The Company may impose penalties in accordance with its work rules for any breach of contract.
In case of contract violation, the Company may impose penalties in accordance with the work rules and, depending on the seriousness of the situation, may pursue criminal liability. The Company uses various meetings to educate employees from time to time, including the protection of business secrets, access control rules, and the principle of disclosing information to the outside world, etc., so that employees can establish correct concepts and develop good working habits.
02
Device Control
The Company’s computer equipment must be installed with antivirus software. The system will determine that the computer meets the specifications before granting network connection authorization. Any unauthorized computer equipment is strictly prohibited from accessing the Company’s network, and the system will automatically block any unauthorized equipment to prevent non-compliant computer devices from affecting the Company’s internal network and equipment.
03
Access Management
To avoid theft and fraudulent use of accounts, Company employees are required to pass two-factor authentication (system account password + OTP one-time password) to access their personal computers. Each R&D project has strict permission control. Project members are required to submit a form to apply for access privileges. The information management staff will set the access privileges after the supervisor’s approval. Access privileges are reviewed once every six months to ensure the correctness of privilege management.
04
Data Management
The Company’s R&D-related data are stored in dedicated storage devices with high-availability redundancy, and project R&D data are controlled by privileges, allowing only authorized members to access them. The Company’s R&D data has a complete regular backup mechanism and is stored off-site to ensure disaster recovery capability in the event of a disaster.
05
Release Management
When the product is delivered to the customer, the application must be completed. The data will be encrypted by the system and uploaded directly to the dedicated space provided by the Company to the customer for downloading without the intervention of anyone in the industry. This dedicated space only allows the specific IP device connection provided by the customer. The connection opening time is limited to one month.
| Type | Item | Prevention Purpose | Information Security Management Resources Description |
| Employee Management | Information security advocacy | Prevention reduces the chance of getting a virus | Information security advocacy for new hires Regularly share cases of major domestic and international information security abnormalities with employees |
| Device Control | Antivirus software Untrusted device blocking |
Prevention of software virus | Information Security System Procurement and Implementation The system determines that the computer meets the criteria before granting permission to connect to the network. If there is an unauthorized device accessing the system, the network will be blocked. |
| Access Management | Two-factor authentication Project authority control |
Avoid account impersonation |
Two-factor authentication system setup Internal R&D management system development |
| Data Management | Professional Storage Equipment Local redundancy architecture Off-site data backup |
Avoid Data loss |
Professional Storage Equipment Procurement Professional Backup Software Procurement |
| Release Management | Automated system rotation Dedicated encryption space |
Avoid Data breach | Internal shipment management system development When the product is delivered to the customer, an application form is required. After the approval of the relevant supervisor and sales contractor, the system will encrypt the data and upload it directly to the exclusive space provided by the Company for the customer to download without any manual intervention. Exclusive space allows only certain IP devices provided by customers to connect, and the connection opening time is limited to one month. |
Cyber Security Management Execution Overview
On August 5, 2025 the Board of Directors reported the following executive highlights for the year:
| Item | Execution Details | Execution Results |
|
Internal Firewall Replacement and Upgrade |
The existing Internet firewall no longer met performance requirements and posed a single point of failure risk. To ensure operational stability and support the high-volume data transmission needs of advanced process R&D, a replacement and upgrade were planned. The new firewall features enhanced hardware specifications to improve overall network throughput and establishes a redundant architecture to mitigate operational risks caused by single point failures. |
Improved overall operational stability and provided stronger network traffic processing capabilities. |
|
Establishment of a Regular Host Vulnerability Scanning Mechanism |
To prevent high-risk vulnerabilities on critical hosts, the Nessus vulnerability scanning system was implemented. External-facing services and critical internal hosts are scanned on a monthly basis. When high-risk vulnerabilities are identified, security updates are centrally scheduled and applied to remediate system vulnerabilities. |
Vulnerability remediation is performed on a monthly basis, enhancing information security protection for critical hosts and achieving a 100% remediation rate for high-risk vulnerabilities. |
|
ISO 27001 Information Security Certification |
To enhance the Company’s information security management capabilities, the Company worked with a consulting firm to comprehensively review and establish information security management policies, ensuring that the updated policies are effectively integrated into corporate processes and daily operations. By adopting the ISO 27001 international standard, the Company strengthened the information security management across preventive controls, ongoing monitoring, and incident response. |
Successfully obtained ISO 27001 Information Security Certification. |
|
Social Engineering Exercise |
A social engineering exercise was conducted in Q4 2024, during which 367 simulated phishing emails were sent. The overall employee pass rate reached 94.28%. Following the exercise, guidance on responding to social engineering emails was distributed, and information security policies were promoted on the Company’s internal website homepage to further enhance employees’ cybersecurity awareness. |
Improved employees’ ability to respond to phishing emails, with no major information security incidents reported to date. |